It would not be wrong to say that email is one of the most commonly used communication tools, especially during the Covid-19 pandemic when the importance of cybersecurity has increased even more. With this trend, it is inevitable that phishing attacks have become one of the methods targeted by cyber attackers. We all know that everyone in a company, from the CEO to the lowest level employee, uses corporate email, and that correspondence, especially financial transactions, are conducted through these emails.
Cybercriminals are constantly looking for new ways to attack companies. In recent years, they have increasingly turned to Business Email Compromise (BEC) attacks, which target corporate correspondence. This description of this type of attack, prepared by Cyberthint analysts, will also provide you with ideas for protection methods by discussing various recommendations.
A BEC (Business Email Compromise) attack is a cash-oriented type of cyber fraud that targets companies that work with foreign suppliers and make bank transfers. The attacker somehow obtains the email address of a company executive or an employee responsible for financial transactions, whether corporate or public. They then hunt for words such as request, payment, transfer and urgent in email messages. In the final phase, they try to deceive individuals by impersonating them and inserting themselves into conversations in order to transfer the money to their own account.
In addition, attackers can also use the method mentioned to gain persistence in the target organization. After achieving their primary goal of generating illicit income, they can continue the fraudulent conversation and gain unauthorized access to the system by performing various system compromises.
What are BEC (Business E-mail Compromise) Attack Methods?
As mentioned above, Business Email Fraud (BEC), an email-based fraud technique, is designed to allow fraudsters to withdraw money or gain unauthorized access to the organization through payment requests, wire transfer requests. BEC attacks typically rely on the attacker’s ability to impersonate a well-known person in the targeted structure (e.g. CEO) or a trusted external person/partner/organization.
This can be achieved in a variety of ways, but the most common methods have been classified by the FBI Internet Complaint Center IC3 into 5 types of BEC attacks. These are:
CEO Fraud

Attackers identify themselves as the CEO or manager of a company and usually send an email to a person in the finance department, requesting that funds be transferred to the attacker’s account.
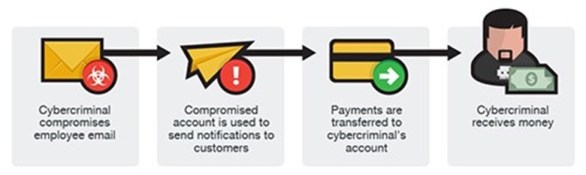
Account Breach

An employee’s account is compromised by the attacker and used to request payments from vendors. The requested payments are sent to the attacker account.
Wrong Invoice Theme
The attacker uses this tactic for foreign suppliers. The fraudster pretends to be the supplier and requests money transfers to fake accounts.
Legal Impersonation

The attacker pretends to be a lawyer or a prosecutor. It is a type of fraud that occurs because low-level employees do not have the knowledge to question the attacker’s claim.
Data Theft

Most of the time, the attacker contacts the CEO and executives in the company via phone/email for personal or private information. In this attack, human resources employees are generally targeted. And uses the information obtained in attacks such as CEO fraud.
The Financial Damages Caused by BEC Attacks on Companies
According to Agari’s cyber intelligence report for 2020, BEC fraudsters currently have central headquarters in at least 39 countries. The average annual damage caused to companies is $26 billion, and these figures are increasing every year.
IC3 reported that there were 23,775 similar cases reported to the FBI in 2019 alone, showing an increase of 3,500 cases and $500 million in damage from 2018.
Research shows that BEC attacks currently make up 40% of global cybercrime losses and have affected at least 177 countries. Additionally, research conducted between May 2019 and July 2020 showed that 50% of attacks occurred in Nigeria, where the first known case of a BEC attack was reported. Below are some examples of high-profile companies that have been targeted by BEC attacks:
-
A cybercriminal purchased a domain name that mimicked a Taiwanese electronics manufacturer and used this domain name for two years to send invoices to large companies, including Facebook and Google, and made $120 million in the process.
-
Cybercriminals who mimicked a construction company persuaded South Oregon University to transfer approximately $2 million to fake accounts.
-
Some fraudsters got involved in correspondence between two football clubs with a domain name that contained the name of one of the clubs but had a different extension. The two clubs, Boca Juniors and Paris Saint-Germain, were discussing the transfer of a player and a commission agreement. As a result, approximately €520,000 went to various fraudulent accounts in Mexico.
-
Toyota’s European branch lost more than $37 million to cybercriminals as a result of a fake bank transfer instruction that an employee mistakenly believed to be real.
In March 2016, some technology companies such as Seagate and Snapchat were also exposed to BEC attacks. It has become inevitable for companies to take precautions against BEC attacks.
Cases of BEC Attacks from Around the World
Below are examples of real-world BEC attack emails that do not include real messages.
CEO Fraud
The attacker poses as the CEO in an attempt to contact a potential victim. The fraudster emphasizes the urgency of the email and the fact that it is not possible to contact the CEO through other channels in order to prevent the recipient from communicating with a real company employee:

Fake Address
A cybercriminal posing as an employee authorized to change bank details from the accounting department writes the following:

Legal Impersonation
The attacker, acting as an executive, convinces the employee to work with a fake lawyer who will contact the employee shortly…

Here, the sender field includes not only the name, but also the fake email address. This attack may not use advanced techniques, but many people can fall into this trap, especially if the real address is not displayed on the recipient’s screen (for example, if it is just too long).
Similar Domain Name
The attacker contacts an employee of the company via email…

The fraudster first registers a domain name similar to the company’s domain (in this case, examp1e.com instead of example.com) and tries to deceive the recipient by hoping that they will not notice the difference.
Key Protection Methods from BEC (Business E-mail Compromise) Attacks
Business E-mail Compromise (BEC) attacks are becoming increasingly common, and organizations need to periodically review their cybersecurity processes to ensure that they are adequately protected. Email processes should be included in this review, and appropriate measures should be integrated into the organization’s structure. Below are some effective methods to protect against BEC attacks:
- Maintain a strong cybersecurity awareness among employees:
- Share tips on cyber hygiene and up-to-date news on scams and fraud.
- Conduct phishing simulations with different scenarios to keep employees aware and prepared for potential attacks.
- Remember that the weakest link in security is the human factor, so provide training on BEC attacks to employees.
- Enforce the use of strong password combinations when setting up accounts.
- Enable two-factor authentication (2FA) for email access and money transfer processes.
- Suspicious or urgent emails should be closely examined:
- Phishing campaign emails are often designed to make the recipient act quickly, so examine the email content closely. Verify that the sender’s email address matches the first message sent to the “To” address when responding.
- Do not rely solely on the sender’s name, and check the email address’s validity from the source.
- Requests for “private” mail conversations should be viewed with suspicion.
- Request verification through a different method of communication, such as a phone call.
- If any suspicion is raised, report it to the IT department for further investigation.
- Know the details and your customers’ habits about why payments are made.
- Verify the accuracy of telephone numbers and payment accounts given in emails.
- Consider using an E-mail Security Gateway product, and activate all detection features with the correct configuration. In this way, administrators can utilize SEG to scan for commonly used BEC incident keywords, such as “payment,” “urgent,” and so on, and highlight emails containing these keywords for additional scrutiny.
- Be cautious of irregular emails sent by executives (C-level). Scrutinize emails requesting money transfers to determine their validity.
- To enable a thorough forensic investigation of a suspected phishing campaign or confirmed incident, it is important that your email infrastructure is capable of retaining audit and access logs for at least six months. However, please note that log retention policies may vary depending on the specific organizational and legal requirements.
- Prohibit automatic email forwarding to third-party addresses. Attackers may try to redirect emails from compromised employee accounts to external locations.
- Use email authentication techniques:
- Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting and Conformance (DMARC) are email authentication techniques that utilize DNS records to provide protection against fraud and phishing.
- DMARC employs SPF and DKIM authentication protocols to verify emails sent from the organization’s domain, as well as prevent malicious actors from reaching users’ primary inbox by blocking fraudulent or phishing emails. As such, organizations can utilize DMARC to mitigate the risk of malicious emails being delivered to their users.
- Avoid including corporate mail groups of critical executives in “To” or “CC” in mailing chains that are sent to external locations as much as possible.

